How Cyber-Resilient is Your 911 Center? Federal Agency Provides No-Cost Guidance
This year marked the 20th anniversary of Cybersecurity Awareness Month (October 2023). There’s never been more or better reasons to prioritize protection against cyber threats and attacks. In 2022, the FBI’s Internet Crime Complaint Center received more than 800,000 complaints, with losses in excess of $10.3 billion.
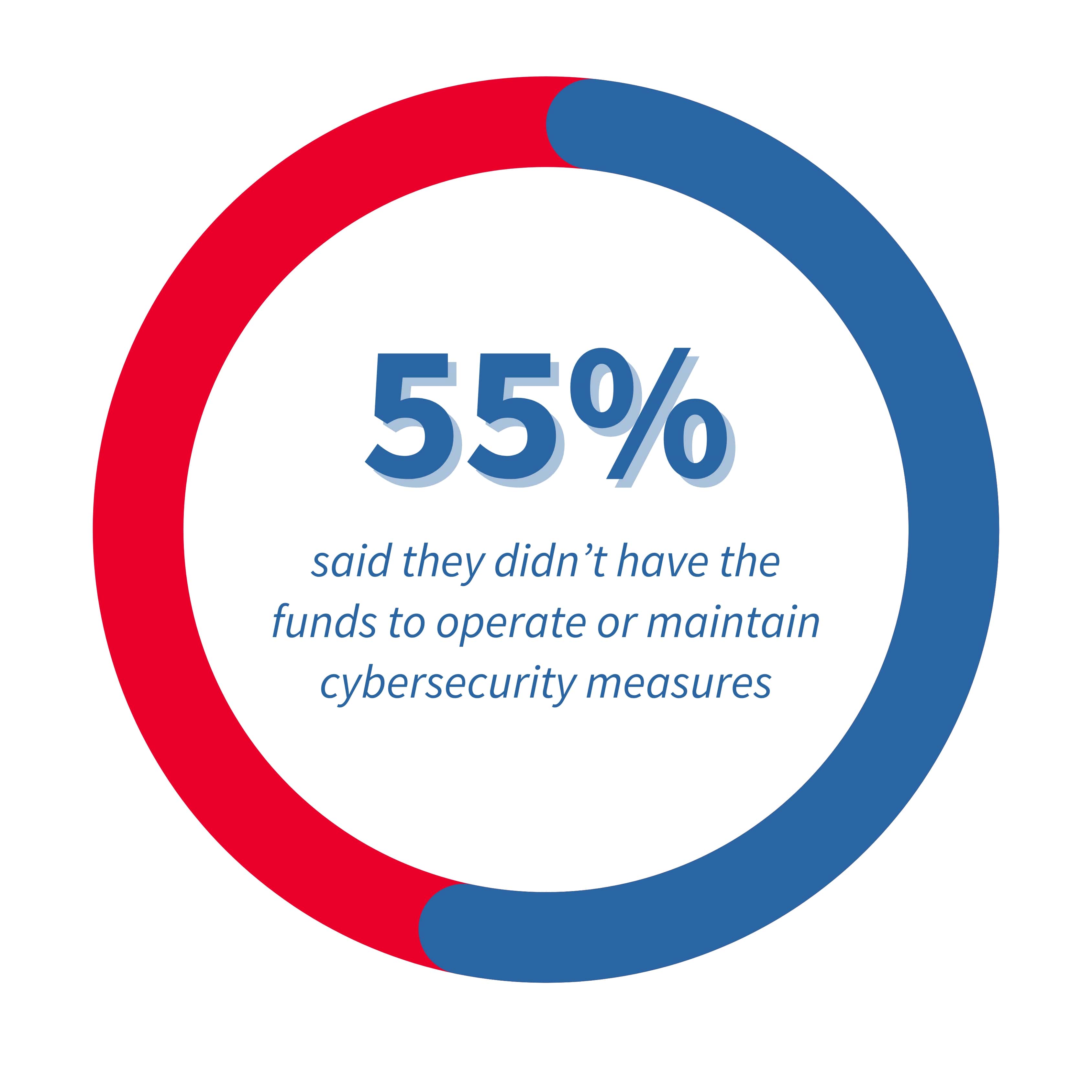
Emergency communications are not immune to cyber-crime, of course, but how well-protected are 911 centers? According to the 2018 SAFECOM Nationwide Survey (SNS) of public safety organizations, 58% of those who responded said they didn’t have funding to invest in cybersecurity, and 55% said they didn’t have the funds to operate or maintain cybersecurity measures. One-third of survey respondents were from 911 centers, while the rest were nearly equally divided among law enforcement, EMS and the fire service. Results from the 2023 survey are expected in early to mid-2024.
The 2018 SNS also found that more than one-third of organizations who responded had experienced a cybersecurity incident that “had an impact on the ability of their emergency response providers and government officials’ ability to communicate over the past five years.”
says Ryan Ford, requirements manager for Cyber Resilient 911 (CR911) at Cybersecurity & Infrastructure Security Agency (CISA). “So no one is really immune from it. It’s a concern for all of us.” Attacks can take the form of Telephony Denial of Service (TDoS), in which a large number of simultaneous calls overloads the network. Ransomware, spear-phishing, malware and swatting, “are all common to 911 centers,” Ford adds.
Next Generation 911 (NG911), the nationwide upgrade of 911 systems to new technologies that enable a wide range of functionality, brings with it, too, greater security. But also vulnerability, in some cases. “One of the advantages of NG911 is the ability to have better interconnectivity between 911 centers,” explains Ford. “That allows the ability to transfer calls to neighboring jurisdictions and transfer the workload” if, for example, your center is overloaded with calls resulting from a natural disaster or another large-scale event. “However,” he adds, “with that increased interconnectedness, there’s an increased threat. A cyberattack in one jurisdiction could introduce vulnerability to another one if they’re connected. And the integration of new technology such as multimedia expands threat vectors.”
So how can you protect your call center?
Ford recommends that every 911 center takes a two-step approach to improve cybersecurity:
Conduct a cyber risk assessment. This process includes identifying network vulnerabilities and threats like unauthorized access to secure information and misuse of data, as well as understanding threats, vulnerabilities and the potential impact of an attack to determine your center’s risk.
Develop specific cyber incident response and vulnerability response plans that guide identification, mitigation, response and recovery from an incident that affects the operation of your center. In the 2018 SNS, just 20% of public safety organizations said they had an incident plan, policy and capabilities in place to respond to a cyberattack or threat.
If you’re not prepared, there’s good news
CISA’s Emergency Communications Division (ECD) can help with a wide range of needs, including no-cost guidance on governance, standard operating procedures, technology and training. ECD offers assistance both virtually and in person to state, local, tribal and territorial (SLTT). 911 centers can contact their Statewide Interoperability Coordinators (SWIC), agency point of contact or Tribal leader to submit a request to ECD.
More resources for 911 centers from CISA, Emergency Communications Preparedness Center (ECPC), SAFECOM and National Council of Statewide Interoperability Coordinators (NCSWIC) include:
SAFECOM: Getting Started with a Cybersecurity Risk Assessment
SAFECOM/NCSWIC: Considerations for Cyber Disruptions in an Evolving 911 Environment
SAFECOM/NCSWIC: Preparing for Technological Transformation in Emergency Communications Centers
Emergency Communications Preparedness Center - an interagency group comprised of 14 federal departments and agencies
The Cyber Resilient 911 (CR911) program, which was launched in early 2022, has started a series of regional symposia as well; these started in late 2023 and will continue into 2024. “We’re reaching out to communication centers to understand their needs,” Ford explains. “Ultimately, we want to offer a range of solutions based on the input we receive.”
And while you’re considering your ECC’s cyber-safety, take a minute to learn the four tips CISA recommends we all follow to keep ourselves protected:
Turn on multi factor authentication
Update your software (as simple as turning off automatic updates)
Think before you click on email
Use strong passwords
To learn more about Cybersecurity Awareness Month, visit CISA.gov.